
Orcus is a remote access Trojan horse with several characteristics. RATs allow attackers to create plugins and offer a powerful core feature set, making them very dangerous malicious programs in this class.
RAT is a pretty stable type that always comes out on top.
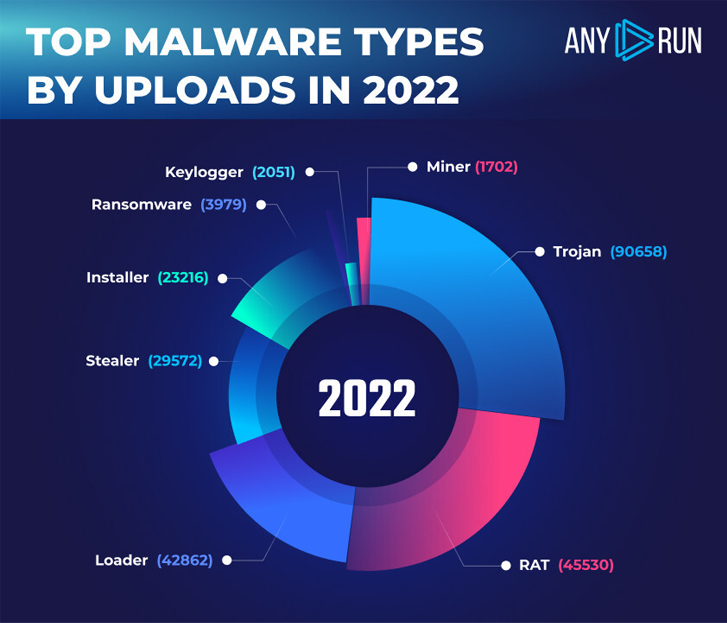 |
| Top Malware Types on ANY.RUN in 2022 |
That’s why you’ll definitely come across this type in your practice, especially the Orcus family. please.
What is the Orcus RAT?
meaningThe Orcus RAT is a type of malicious software program that allows remote access and control of computers and networks. It is a type of Remote Access Trojan (RAT) that has been used by attackers to access and control computers and networks.
functionOnce downloaded to a computer or network, it begins executing malicious code, giving the attacker access and control. It can steal data, conduct surveillance, and launch DDoS attacks.
distributionMalware is commonly spread through malicious emails, websites, and social engineering attacks. They are also often bundled with other malicious software programs such as Trojan horses, worms, and viruses.
Orcus RAT malware analysis life hack
This malware is designed to be difficult to detect as it often uses advanced encryption and obfuscation techniques to prevent detection. It also contains all the data needed for RAT configuration if you need to reach the Orcus core.
There are also a few life hacks to keep in mind when performing Orcus RAT analysis.
Today we will explore the .NET samples available for free download in the ANY.RUN database.
SHA-256: 258a75a4dee6287ea6d15ad7b50b35ac478c156f0d8ebfc978c6bbbbc4d441e1
1 — Understand the Orcus class
You should start by checking for malware classes that can capture hidden program characteristics. The set of data contained in the class is exactly what is useful for research.
The Orcus.Config namespace has the following classes:
- constant: Orcus file and directory data. For example, the path to a file where the user’s keystrokes are stored, or the path to the directory where the plugins used in the examples reside.
- Configuration: Contains wrapper methods for decrypting malware configurations and their plugins.
- Configuration data: A static class with only encrypted malware and plugin configuration fields.
2 – Find the Orcus RAT resource
when you dive into Configuration class, you can notice GetDecryptedSettings Method.Later, it AES. DecryptAnd it looks like your job is done and you’ve finally found the malware configuration.But wait – it’s not included in the assembly Orcus.Shared.Encryption namespace.
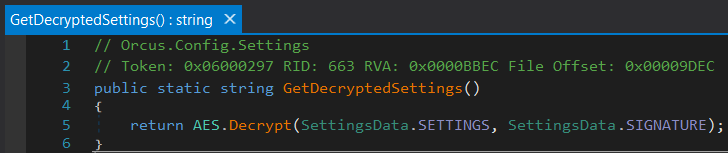 |
| GetDecryptedSettings method |
The Orcus RAT uses the ‘deflate’ algorithm to store additional assemblies within the malware resource. You can find the required assembly by going to Resources. Unzipping them reveals the decryption algorithm used by the Orcus sample. That’s it for one more lifehack of the day.
3 — Decrypt data
Configuration data is encrypted, so the treasure hunt continues.
Orcus RAT encrypts data using the AES algorithm and encodes the encrypted data using Base64.
How to decrypt the data:
- Generates a key from the given string using Microsoft’s PBKDF1 implementation
- Decode data from Base64
- Apply the generated key to decrypt data via AES256 algorithm in CBC mode.
As a result of decoding, we get the malware configuration in XML format. And all the secrets of Orcus are in your hands.
Get it once in the malware sandbox
Malware analysis is not an easy task. Cracking a sample definitely takes time and effort. That’s why it’s always great to stand out. Get everything at once and in a short amount of time. The answer is simple. By using a malware sandbox.
The ANY.RUN malware sandbox automatically picks up the Orcus RAT configuration. A much easier way to analyze malicious objects. Try it now. The service has already pulled all the data from this Orcus sample, so you can enjoy a smooth investigation.
⚡ write “”hacker news 1” Get ANY.RUN Premium Subscription FREE for 14 days when you enter the promo code at support@any.run using your company email address!
Conclusion
While Orcus RAT masquerades as a legitimate remote administration tool, it is not intended to be, as evidenced by its features and functionality. Malware analysis helps to obtain information about a company’s cybersecurity.
Protect your business from this threat. Implement a comprehensive security strategy, train your employees to recognize and avoid malicious emails and websites, and deploy Orcus with a trusted antivirus and ANY.RUN malware sandbox. Detect and analyze.











