
The use of Software as a Service (SaaS) is growing rapidly and shows no signs of slowing down. Its decentralized and easy-to-use nature helps improve employee productivity, but it also poses many security and IT challenges. Keeping track of all SaaS applications that have access to your organization’s data can be a daunting task. Understanding the risks that SaaS applications pose is equally important, but protecting the invisible can be difficult.
Many organizations implement access management solutions, but these limit visibility to pre-approved applications only. The average medium-sized organization has hundreds, possibly thousands, of SaaS applications that bypass IT and security entirely and are either for quick and easy solutions or for employees who have found a free version. employed by members. This poses a significant risk as many of these applications do not have the required security and/or compliance standards but still have access to the organization.
⚡ wing security recently announced the availability of its SaaS application detection engine as a free self-service product. This tool is designed to help companies identify risky SaaS applications that employees have adopted outside of company policy.
Democratizing SaaS Discovery
The risks associated with SaaS Shadow IT have become more common in recent years due to the widespread use of SaaS within organizations. However, many of the security solutions available in the past focused on making security teams aware of problems rather than providing in-product or automated remediation capabilities. In fact, the first step in dealing with SaaS-related risks is to have a clear understanding of his SaaS stack in use within the organization. This information should be easily accessible and as easy to navigate as the SaaS application itself.
To give security teams better visibility and understanding of the risks associated with increased SaaS usage, Wing Security (Wing) has decided to offer its SaaS Discovery tool as a free self-service product . saw hereThe company aims to give security teams a comprehensive view and better understanding of the SaaS applications in use within their organizations, regardless of size or budget.
What is included in the Wing Security Free edition?
- Fast and easy self-onboarding.
- An easy-to-understand dashboard view of SaaS applications (including third-party applications) in use within your organization.
- Risky applications are flagged in the system
- Details of the compliance each SaaS application meets, how it connects to your organization, the permissions granted, and who is using them (first 100 applications).
- Wing Security’s reputation score for each SaaS application is expressed as ‘shields’ with 0 to 3 shields.
- Classification and tagging options.
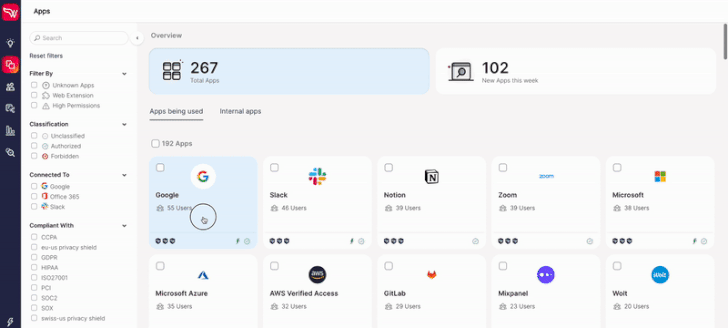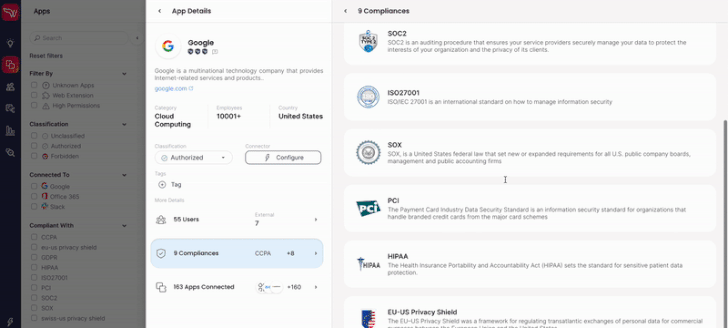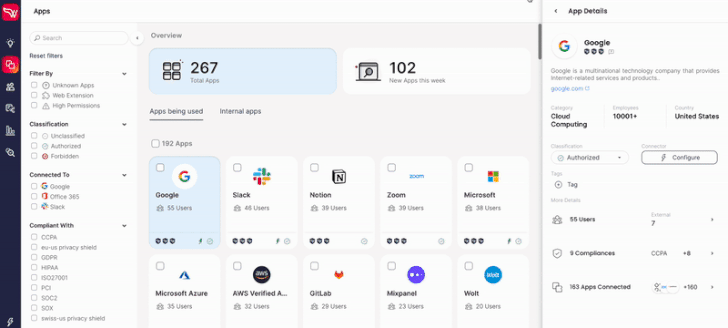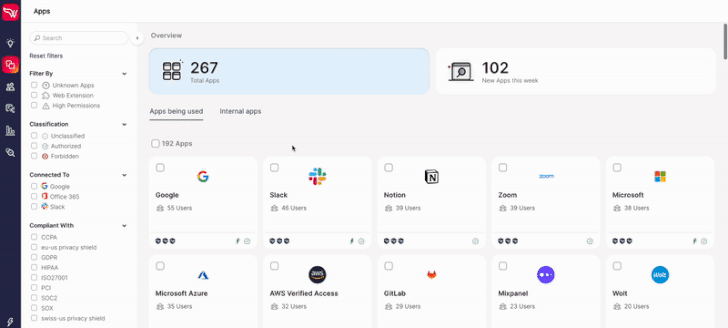 |
| Wing security free version. |
Non-intrusive detection: no agents, no proxies
Understanding that a modern security solution should never get in your way is at the heart of Wing Security’s new service. To plan his organization’s use of SaaS applications, Wing uses APIs to connect to key IT-approved SaaS applications. These are commonly used applications in nearly every environment, including Google, Office 365, Salesforce, GitHub, Slack, and more.
Wing can then map all SaaS applications connected to these applications and the applications connected to them. SaaS applications are interconnected in a huge mesh, creating a “shadow network” of connections. This shadow network is used by Wing for application mapping, but it can also be a security concern as it can be used for lateral movement within your organization. As a complete enterprise service, Wing maps all users using these applications, the data that exists within and across these applications, and provides near real-time security updates when the applications in use are compromised. Provides alerts.
 |
| Wing Security “connects” to SaaS applications via APIs |
What are your users asking for?
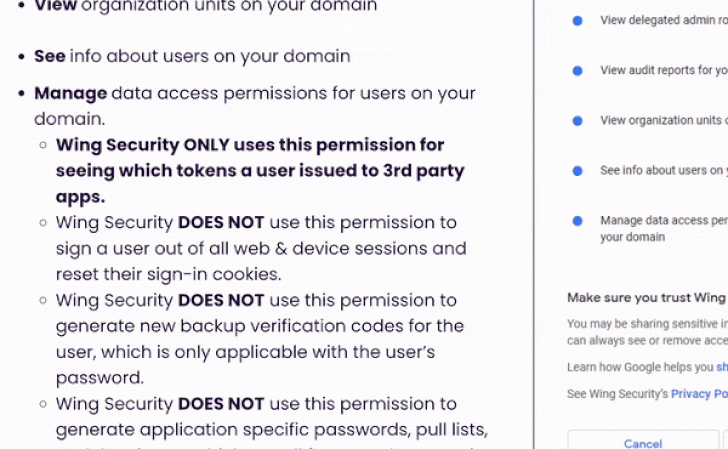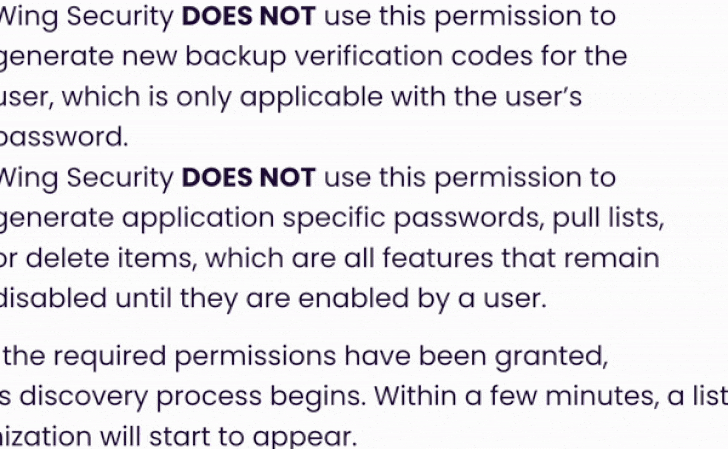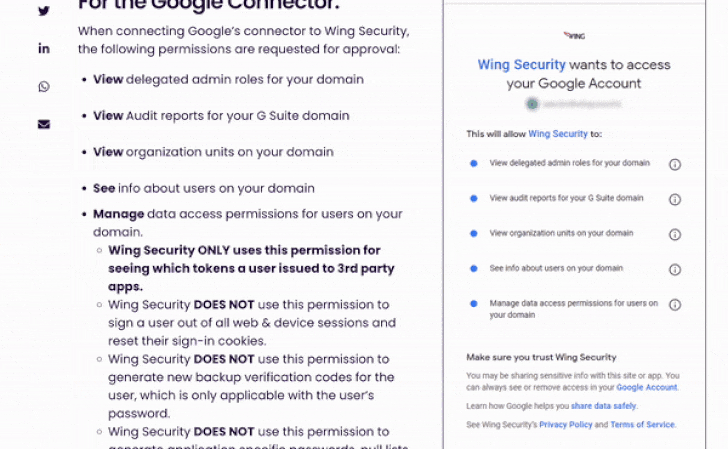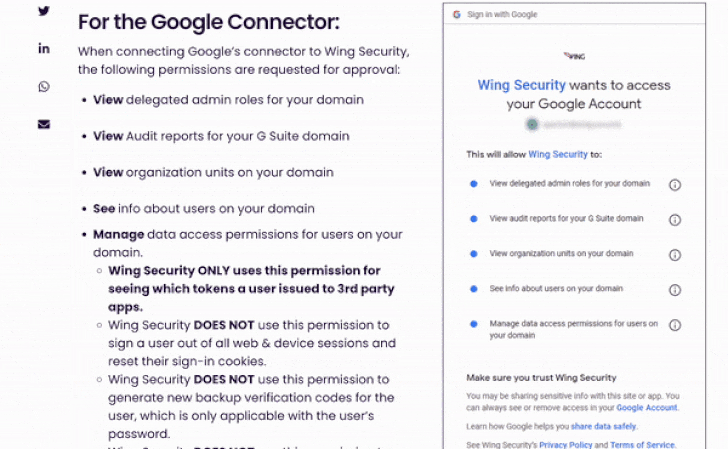
In line with Wing Security’s non-intrusive discovery, Wing Security Free edition requires very basic permissions that can be granted by an organization’s super administrator.
Most of the required permissions are read-only. There is one authority of his within Google that requires “administrative” access to allow Wing visibility into the tokens users have issued to third-party apps.Wing security mention on the relevant product page Keeping customer data safe is a priority and we provide compliance in place for data security.
What is “SaaS”?
The term SaaS has traditionally been abbreviated, S.software as a S.services, all modern SaaSS.may mean “service”. There are three types of his SaaS that are commonly used these days.
- Widely used enterprise SaaS, mostly with paying users, such as Stack, Dropbox, Google, and Microsoft.
- Lesser-known niche SaaS for specific industries, such as Figma and Canva for design, outreach for sales, and Github for engineers. Wings of SaaS security. These SaaS users can include both paid and free users.
- A completely free app for personal use, probably unknown to others. It also includes apps that you signed up for a free trial and for some reason forgot about.
These are the three main types of SaaS applications, but they are like markers on the spectrum. SaaS applications regularly move up and down this spectrum as companies grow and evolve. However, as long as these applications are logged in using your organization’s email, they will be detected by Wing Security Free Discovery.
What more is available in the paid version of Wing Security?
The paid version of Wing Security is called Wing Security Enterprise Edition and includes everything in the free version plus:
- Deeper SaaS detection, including detection of all browser extensions and all kinds of locally installed or internally developed SaaS applications
- Monitoring sensitive data shared by SaaS applications. Example: AWS key shared in public Slack channel.
- Manage user-related risks such as excessive permissions, mismatched users, or abnormal usage.
- Real-time threat intelligence alerts and actionable updates when SaaS apps used within your organization are the party to a breach or cyberattack.
- repair tool. Many of the issues discovered by Wing Security can be resolved with just a few clicks within Wing’s easy-to-use interface, without the need for manual resolution.
- Built-in automation tools. Some of his SaaS security issues can be pervasive, with thousands of repeated instances of the same issue found. Trying to fix the problem manually could take years. With Wing’s built-in automation tools, you can solve such cases in minutes with just a few clicks. New instances of the same issue may reappear in the future, so long-term protection is enabled by setting policies that Wing Security will help you call.
- End User Engagement. A nice additional detail within the Wing interface is the ability to set up automation to include keeping the end user in the loop. simply notify us of the problem and how to fix it, or[承認]Click to let automation solve the problem. If the user ignores or misses the message, by default the task will automatically “approve” after a certain amount of time.
In summary, Wing Security’s new tool addresses the growing use of SaaS and the security and IT challenges it poses by tracking which SaaS applications have been granted access to an organization’s data. The free version includes a quick and easy self-onboarding process, an easy-to-use dashboard view of the SaaS applications in use, risky application notifications, compliance and permissions information, and a reputation score for each application . The tool uses a non-intrusive method of connecting to leading IT-approved SaaS applications using APIs to map an organization’s use of his SaaS applications without causing disruption.
For more information on Wing Security’s new free SaaS Discovery solution, click here.











