A new Golang-based information-stealing malware called titan stealer Promoted through Telegram channel by threat actors.
Uptycs security researchers Karthickkumar Kathiresan and Shilpesh Trivedi said: Recent report.
Details of the malware were first documented in November 2022 by cybersecurity researcher Will Thomas (@BushidoToken) by querying IoT search engine Shodan.
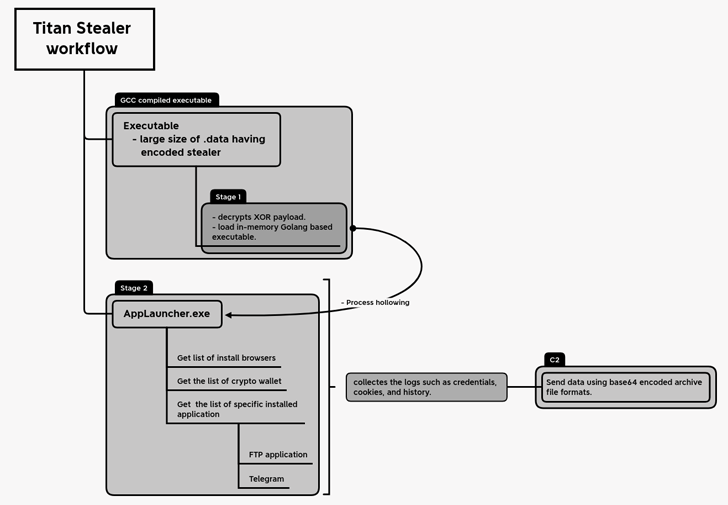
Titan is offered as a builder, allowing customers to customize the malware binary to include specific functionality and types of information to steal from the victim’s machine.
At runtime, the malware uses a technique called process hollowing to inject its malicious payload into the memory of a legitimate process called AppLaunch.exe, a Microsoft .NET ClickOnce Launch Utility.
Major web browsers targeted by Titan Stealer include Google Chrome, Mozilla Firefox, Microsoft Edge, Yandex, Opera, Brave, Vivaldi, 7 Star Browser and Iridium Browser. The crypto wallets selected are Armory, Armory, Bytecoin, Coinomi, Edge Wallet, Ethereum, Exodus, Guarda, Jaxx Liberty, and Zcash.
It can also collect a list of applications installed on compromised hosts and capture data related to the Telegram desktop app.
The collected information is sent as a Base64-encoded archive file to a remote server under the attacker’s control. Additionally, the malware comes with a web panel that allows attackers to access the stolen data.
The exact method used to distribute the malware is still unknown, but traditionally attackers have used a variety of methods including phishing, malicious advertising, and cracked software.
“One of the main reasons [threat actors] In his own analysis of the Titan Stealer, Cyble notes that Golang makes it easy to create cross-platform malware that can run on multiple operating systems, including Windows, Linux, and macOS. There is a possibility that
“Furthermore, binary files compiled with Go are smaller, making them more difficult for security software to detect.”
The development comes just over two months after SEKOIA detailed another Go-based malware called Aurora Stealer that several criminals are using in their campaigns.
Malware is usually spread through look-alike websites of popular software, and the same domains are actively updated to host trojanized versions of various applications.
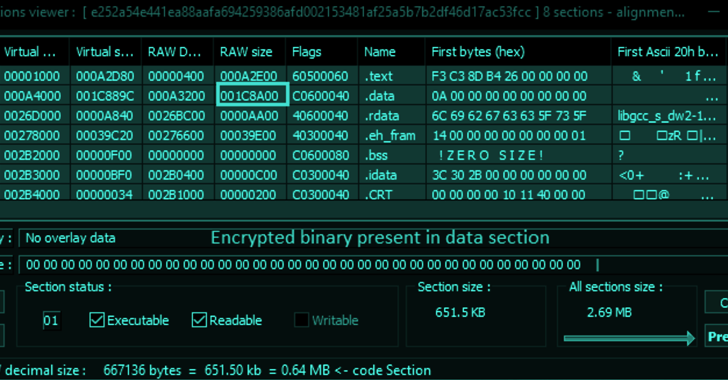
It has also been observed to artificially inflate the size of the executable up to 260MB by adding random data to avoid detection by antivirus software using a method called padding.
The findings follow malware campaigns observed to deliver Raccoon and Vidar using hundreds of fake websites masquerading as legitimate software and games.
In an analysis released earlier this month, Team Cymru said, “Vidar operators have split their infrastructure into two parts: one dedicated to their regular customers and one dedicated to their management team, potentially I’m also a premium/important user.”











