Microsoft announced on Tuesday that the fake Microsoft Partner Network (MPN) was used to create a malicious OAuth application as part of a malicious campaign designed to compromise an organization’s cloud environment and steal email. We have announced that we have taken steps to deactivate the account.
“The applications created by these scammers were then used in consent phishing campaigns to trick users into giving them access to the scam apps,” said the tech giant. “This phishing campaign primarily targeted some customers based in the UK and Ireland.”
Consent phishing is a social engineering attack where users are tricked into granting permissions to malicious cloud applications. The application is weaponized and gains access to legitimate cloud services and sensitive user data.
Windows makers said they became aware of the campaign on December 15, 2022. We have since emailed affected customers, noting that the attackers abused their consent to steal their mailboxes.
In addition, Microsoft said it has implemented additional security measures to improve the vetting process associated with the Microsoft Cloud Partner Program (formerly MPN) and to minimize the potential for future fraud. .
This disclosure is consistent with a report released by Proofpoint about how attackers successfully exploited Microsoft’s “Verified Publisher” status to gain access to an organization’s cloud environment.
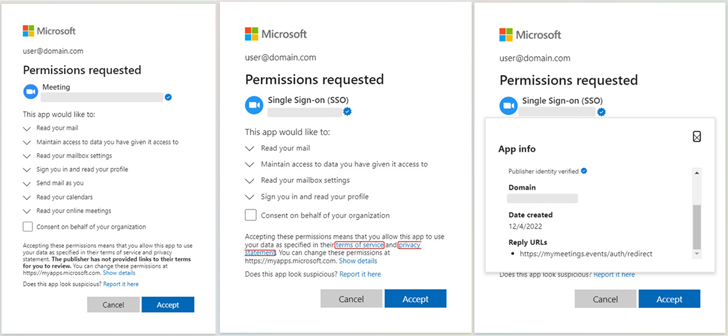
What’s notable about this campaign is that it successfully tricked Microsoft into obtaining a blue verified badge by mimicking a popular brand. “The attacker used a rogue partner’s account to add a verified publisher to his OAuth app registration created in Azure AD,” the company explained.
First observed on December 6, 2022, these attacks used look-alike versions of legitimate apps such as Zoom to trick targets into granting access and facilitating data theft. Targets included finance, marketing, managers, and senior management.
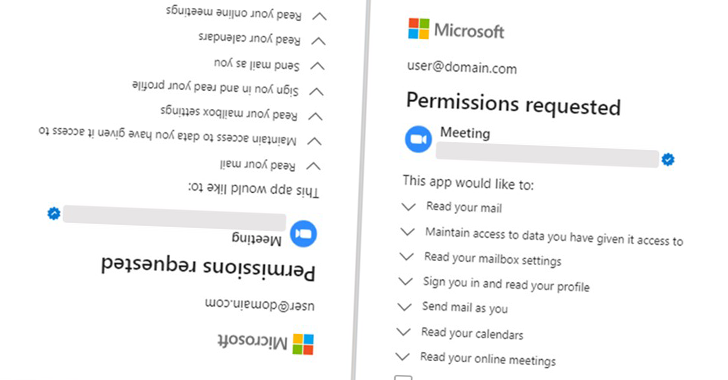
Proofpoint said a malicious OAuth app could have “broad delegated permissions” such as reading email, adjusting mailbox settings, and gaining access to files and other data connected to a user’s account. I pointed out that I have a
And unlike previous campaigns that compromised existing Microsoft Verified Publishers and leveraged OAuth app permissions, the latest attacks impersonate legitimate publishers to become verified and distribute rogue apps. It also states that it is designed for
Two of the apps in question were named “Single Sign-on (SSO)”, while the third was called “Meeting” and was masquerading as video conferencing software. All three of his apps, created by three different publishers, targeted the same company and utilized the same attacker-controlled infrastructure.
“Potential impacts on organizations include compromised user accounts, data exfiltration, misuse of disguised organizational branding, business email compromise (BEC) fraud, and mailbox abuse.” says the enterprise security company.
The campaign is said to end on December 27, 2022. This is because Proofpoint notified his Microsoft of the attack on December 20th and the app was disabled.
Our findings demonstrate the sophistication of these attacks, not to mention circumventing Microsoft’s security protections and exploiting the trust users place in enterprise vendors and service providers.
This isn’t the first time a fake OAuth app has been used to target Microsoft’s cloud services. In January 2022, Proofpoint detailed another threat campaign called OiVaVoii. It targeted senior management and took control of their accounts.
Then, in September 2022, Microsoft revealed it dismantled an attack that leveraged a rogue OAuth application deployed on a compromised cloud tenant to ultimately take control of Exchange servers and distribute spam. Did.











