
A critical flaw in Progress Software’s MOVEit Transfer managed file transfer application has been widely exploited to take over vulnerable systems.
This shortcoming is related to a severe SQL injection vulnerability, which has not yet been assigned a CVE identifier, but which could lead to privilege escalation and potentially unauthorized access to your environment.
“A SQL injection vulnerability has been discovered in the MOVEit Transfer web application that could allow an unauthenticated attacker to gain unauthorized access to MOVEit Transfer’s database,” the company said.
“Depending on the database engine used (MySQL, Microsoft SQL Server, or Azure SQL), an attacker could execute SQL statements that modify or delete database elements, as well as infer information about the structure and contents of the database. There is a possibility.”
A patch for this bug is available in the following versions by the Massachusetts company that also owns Telerik: 2021.0.6 (13.0.6), 2021.1.4 (13.1.4), 2022.0.4 (14.0.4) ), 2022.1.5 (14.1.5), and 2023.0.1 (15.0.1).
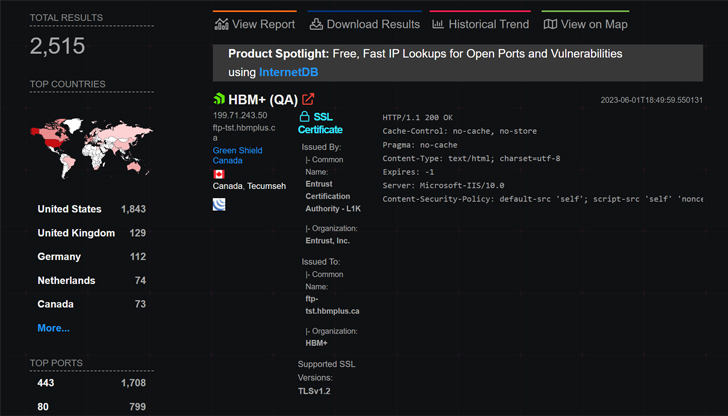
This development was first reported by Bleeping Computer. According to Huntress and Rapid7, as of May 31, 2023, approximately 2,500 MOVEit Transfer instances have been exposed to the public internet, with the majority located in the United States.
A successful exploitation attempt will result in a “human2.aspx” in a “wwwroot” directory created by a script with a randomized filename to “extract various data stored by the local MOVEit service”. A web shell named file will be expanded.
The web shell is also designed to add a new admin user account session named “Health Check Service” to avoid detection. analysis The actual state of the attack chain has been clarified.
Threat intelligence firm GreyNoise said, “As of March 3, 2023, we observed scanning activity on the login page of MOVEit Transfer at /human.aspx,” adding that it “scanned five different sites trying to discover MOVEit’s installation location.” IP address detected.” “
🔐 Mastering API Security: Understanding Your True Attack Surface
Discover untapped vulnerabilities in your API ecosystem and take proactive steps towards ironclad security. Join us for an insightful webinar!
join the session
Satnam Narang, senior staff research engineer at Tenable, said, “Although the details of the group behind the zero-day attacks involving MOVEit are unknown, this confirms an alarming trend of threat actors targeting file transfer solutions. I will.”
In response, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued an alert urging users and organizations to follow mitigation procedures to protect against malicious activity.
We also recommend isolating your servers by blocking inbound and outbound traffic, inspecting your environment for possible indicators of compromise (IoCs), and removing any that exist before applying the fix. .
Security researcher Kevin Beaumont said, “If this turns out to be a ransomware group again, this will be the second enterprise MFT zero day in a year. cl0p recently went wild on GoAnywhere.” Stated.











