
Cyberattacks using infected USB-infected drives as an initial access vector tripled in the first half of 2023.
This is according to a new Mandiant study detailing two such campaigns: Story and snow drive – Covers both public and private sectors worldwide.
SOGU said it was “the most prevalent USB-based cyber espionage attack using USB flash drives and one of the most aggressive cyber espionage campaigns targeting both public and private sector organizations worldwide across industries. One,” said a Google-owned threat intelligence firm.
The activity is believed to come from a China-based cluster called TEMP.Hex, also tracked by the names Camaro Dragon, Earth Preta, and Mustang Panda. Coverage includes construction, engineering, business services, government, healthcare, transportation and retail in Europe, Asia and the United States.
The infection chain detailed by Mandiant shows tactical similarities to another Mustang Panda campaign uncovered by Check Point. The campaign uncovered a self-propagating malware called WispRider that spreads via compromised USB drives and can infiltrate air-gapped systems.
It all starts with a malicious USB flash drive plugged into your computer, PlugX (aka Korplug) runs, then decrypts and launches a C-based backdoor called SOGU, extracting the desired files, keys, etc. Steal strokes, screenshots.
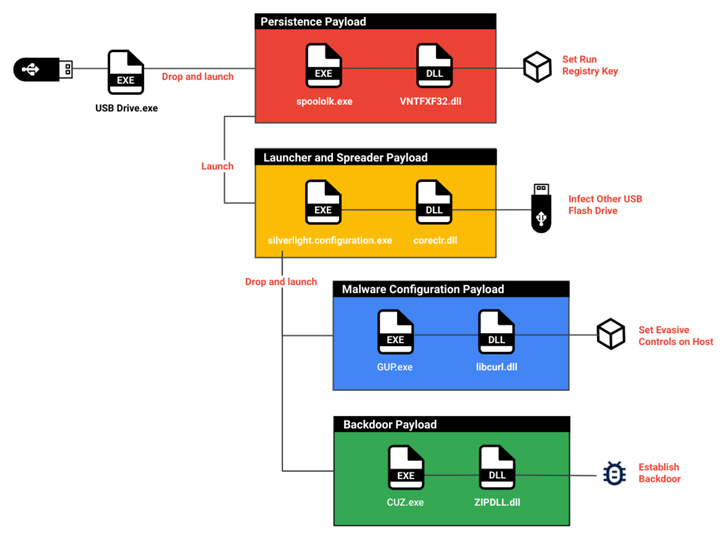
SNOWYDRIVE TARGETS ASIAN OIL AND GAS ORGANIZATIONS
The second cluster utilizing the USB intrusion mechanism is UNC4698. UNC4698 singles out Asian oil and gas organizations to deliver SNOWYDRIVE malware and execute arbitrary payloads on hacked systems.
Shielding Against Insider Threats: Mastering SaaS Security Posture Management
Worried about insider threats? We’ve got you covered! Join us for this webinar to explore practical strategies and proactive security secrets using SaaS Security Posture Management.
join today
“Once SNOWYDRIVE is loaded, it creates a backdoor in the host system that allows an attacker to remotely issue system commands,” said Mandiant researchers Rommel Joven and Ng Choon Kiat. rice field. “It also spreads to other USB flash drives and propagates throughout the network.”
In these attacks, the victim was tricked into clicking on a boobytrapped file disguised as a legitimate executable, thereby performing a series of malicious actions starting with the dropper gaining a foothold and executing the SNOWYDRIVE implant. is started.
Backdoor functionality includes performing file and directory searches, uploading and downloading files, and launching reverse shells.
“Organizations should prioritize implementing access restrictions to external devices such as USB drives,” the researchers said. “If that’s not possible, devices should at least be scanned for malicious files and code before connecting to the internal network.”











