Ukraine suffered a new cyber attack from Russia dubbed a previously undocumented Golang-based data wiper. swift slicer.
ESET has identified the attack as being carried out by Sandworm, a national group associated with military unit 74455 of the Main Intelligence Service of the General Staff Headquarters (GRU) of the Russian Federation.
“When executed, it will delete shadow copies, recursively overwrite files in %CSIDL_SYSTEM%\drivers, %CSIDL_SYSTEM_DRIVE%\Windows\NTDS, and other non-system drives, and restart the computer.” ESET disclosed in a series of tweets
Overwriting is accomplished by filling a 4,096-byte long block with a randomly generated sequence of bytes. The intrusion he discovered on January 25, 2023, added the Slovak cybersecurity firm.
Sandworm, also tracked under the names BlackEnergy, Electrum, Iridium, Iron Viking, TeleBots, and Voodoo Bear, has been conducting disruptive and destructive cyber campaigns targeting organizations around the world since at least 2007. There is history.
The threat actor’s sophistication is evidenced by multiple separate kill chains comprised of various custom tools such as BlackEnergy, GreyEnergy, Industroyer, NotPetya, Exaramel, and Cyclops Blink.
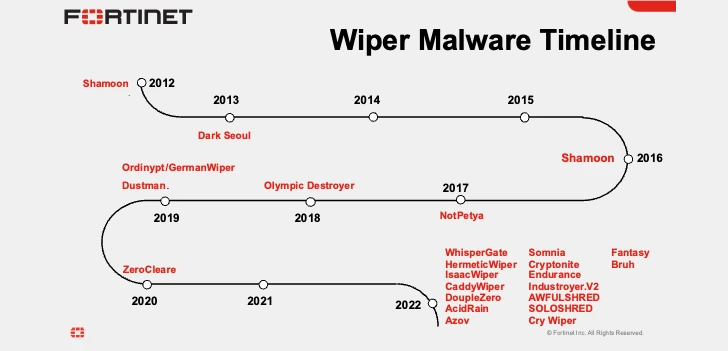
In 2022 alone, Sandworm unleashed WhisperGate, HermeticWiper, IsaacWiper, CaddyWiper, Industroyer2, Prestige, and RansomBoggs against Ukraine’s critical infrastructure, coinciding with Russia’s military invasion of Ukraine.
Fortinet FortiGuard Labs researcher Geri Revay said in a report published this week: “It’s hardly monetizable. The only viable use cases are subversion, sabotage, and cyber warfare.”
The SwiftSlicer discovery demonstrates the consistent use of wiper malware variants by Russian adversaries in attacks aimed at wreaking havoc in Ukraine.
The development also stems from the Ukrainian Computer Emergency Response Team (CERT-UA) linking Sandworm to a recent and largely unsuccessful cyberattack against the state-owned news agency Ukrinform.
Intrusions suspected to have been carried out by December 7, 2022 used five different data wipers (CaddyWiper, ZeroWipe, SDelete, AwfulShred, and BidSwipe) targeting Windows, Linux, and FreeBSD systems. I was. .
“It has been established that the final stage of the cyber attack began on January 17, 2023,” CERT-UA said in its advisory. “But we’ve had only partial success, especially with some data storage systems.”
Sandworm isn’t the only one looking to Ukraine. Other Russian government-backed actors, including APT29, COLDRIVER, and Gamaredon, have actively targeted various Ukrainian entities since the beginning of the war.











